
The Indigo observatory
I am inviting you to the Indigo Observatory, a peculiar corner of the internet where current events get filtered through Discworld metaphors, and where watching the status quo maintain itself becomes both entertaining and only slightly depressing. If you are looking for breathless enthusiasm about how technology and politics are definitely getting better, it is not for you. If you want someone to point out that Lord Vetinari’s approach to governance looks suspiciously like modern Western democracies, whilst finding this observation darkly amusing, then grab a cup of tea and settle in. ...

NIS2 compliance: The Kafkaesque burden on Europe’s companies
Europe mandates hundreds of thousands of companies to meet stringent cybersecurity standards, yet the auditor pool is woefully small.
Cloud-on-prem vs Big Tech
An uncomfortable truth: Every byte uploaded to AWS, Azure, or Google Cloud isn’t just data, it’s cloud capital. Coined by economist Yanis Varoufakis, the term captures how tech giants transform your digital activity into privatised infrastructure. It’s not merely about hosting files; it’s about hoarding power. And right now, the US holds the keys, turning Europe into a lodger in its digital manor. But there is an alternative: cloud-on-prem, a return to digital self-sufficiency, and European providers like Hetzner, who offer control, compliance, and a way to starve the beast. Think of it less as going backwards and more as refusing to pay rent to your colonial landlord. ...
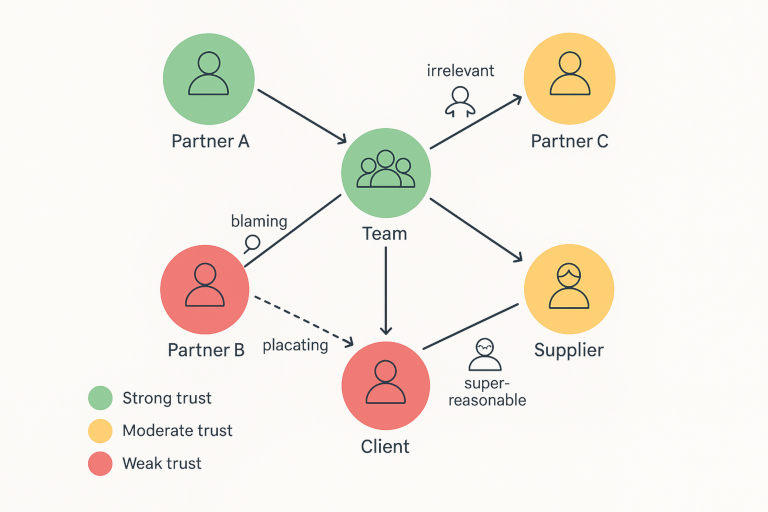
Mapping trust
Organisations invest heavily in procedures, certifications, and standards. Yet whether those investments deliver results depends on something far less tangible: human relationships. As organisations become more distributed and interdependent, seeing and strengthening these connections becomes critical to resilience. The hidden architecture of trust Without trust, perfectly drafted policies and shiny certificates become little more than beautifully formatted PDFs. In networks where multiple organisations or teams rely on each other to deliver quality services, trust determines whether processes work in practice or collapse under miscommunication. ...

The future will surprise us. Be prepared.
When scenario planning practitioners and others speak of “looking forward”, they don’t mean prediction. Forecasting implies we know where we’re going, while scenario planning admits we do not. Looking forward is not clairvoyance, nor is it the worship of trend graphs. It is not about guessing which shiny technology or geopolitical shift will “win”. Like a single renewable technology or control system which will dominate the grid. That kind of forward-looking, the PowerPoint prophecy, breeds false certainty. ...
The relational firewall
A developer pushes a feature. Security flags a missing TLS configuration. Operations scrambles to patch the database. Alerts multiply while emails ping insistently and no one knows who owns what. Technical pipelines are fine. The human side stutters. Miscommunication, conflicting priorities, and unspoken assumptions slow down response and occasionally create a small drama worthy of a sitcom. DevOps, Security, and Ops can be aligned by noticing patterns in how teams interact under stress, practising adaptive responses, and embedding relational awareness into everyday workflows. The goal is operational harmony without the motivational poster clichés or mandatory soft-skills seminars. ...
Muscle memory for incident stress
Introduction A SOC alert does not knock politely. It arrives like a crowd of people shouting different instructions in a language only half understood. One alert maybe says “ransomware detected,” another could flag “unusual login,” and the logs you trust most are blank. Analysts glance at dashboards, shrug, and whisper to each other over Teams while the CISO insists on updates every five minutes. Virginia Satir’s work gives us a lens for understanding this chaos. She mapped how people respond to stress, communicate under pressure, and shape collective outcomes. Her stances, emotional congruence, and relational awareness offer a way to train teams not just to follow procedures, but to survive pressure without fracturing. ...
The audit as x-ray
There is a certain bleak poetry in a security audit. The word audit evokes clipboards, compliance spreadsheets, and the faint smell of burnt patience. But beneath the bureaucracy lies something far more interesting: an act of seeing. A real audit, not compliance theatre, but the kind that leaves everyone quietly re-evaluating their life choices, is less about ticking boxes than about mapping the hidden currents that actually keep an organisation secure. Which is why it belongs not in the company of frameworks, but in the orbit of Virginia Satir, Eyal Weizman, and Trevor Paglen. ...
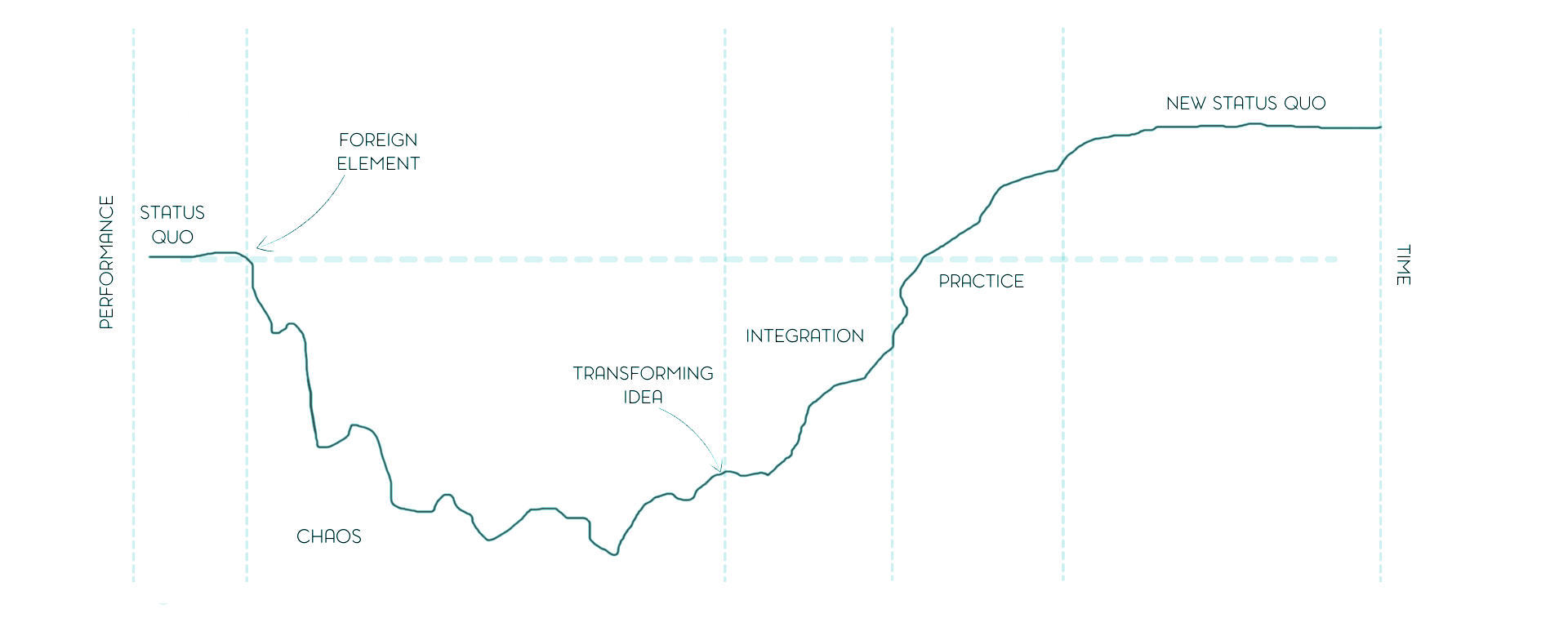
How to survive your first incident response
If you have ever tried to set up a Security Incident Response Team (SIRT) function in a small organisation, you will know that it is not about security, incidents, or even teams. It is about humans behaving badly under stress. Enter the Satir Change Model, a tool from family therapy that has no right working in cybersecurity, and yet works better than most “cyber resilience frameworks”. Her five-stage model maps beautifully onto what happens when a small organisation suddenly decides to “get serious about incident response”. Building a SIRT is not about defeating chaos; it is about becoming fluent in it. And once you have done that, “It cannot get any worse” stops being a threat and starts being the team motto making people laugh, sending extra oxygen to their brain. ...

The compliance email and the collective flinch
Ever received that little gem of an email from IT: “Compliance Reminder”? No greetings, no sugar-coating, just a tiny, accusatory phrase in your inbox like a foghorn in a library. And just like that, the office collectively holds its breath. Instantly, a strange ritual begins. Even the most relaxed of colleagues, those who haven’t touched the company VPN in months, start opening folders, scanning drives, and muttering about forgotten passwords like they’re uncovering ancient curses. Karen from marketing begins tearing through her emails as though the server itself might collapse if she doesn’t click the right links. Greg in finance panics at a spreadsheet he hasn’t touched since 2019, convinced it’s harbouring hidden sins. ...