How to survive your first incident response
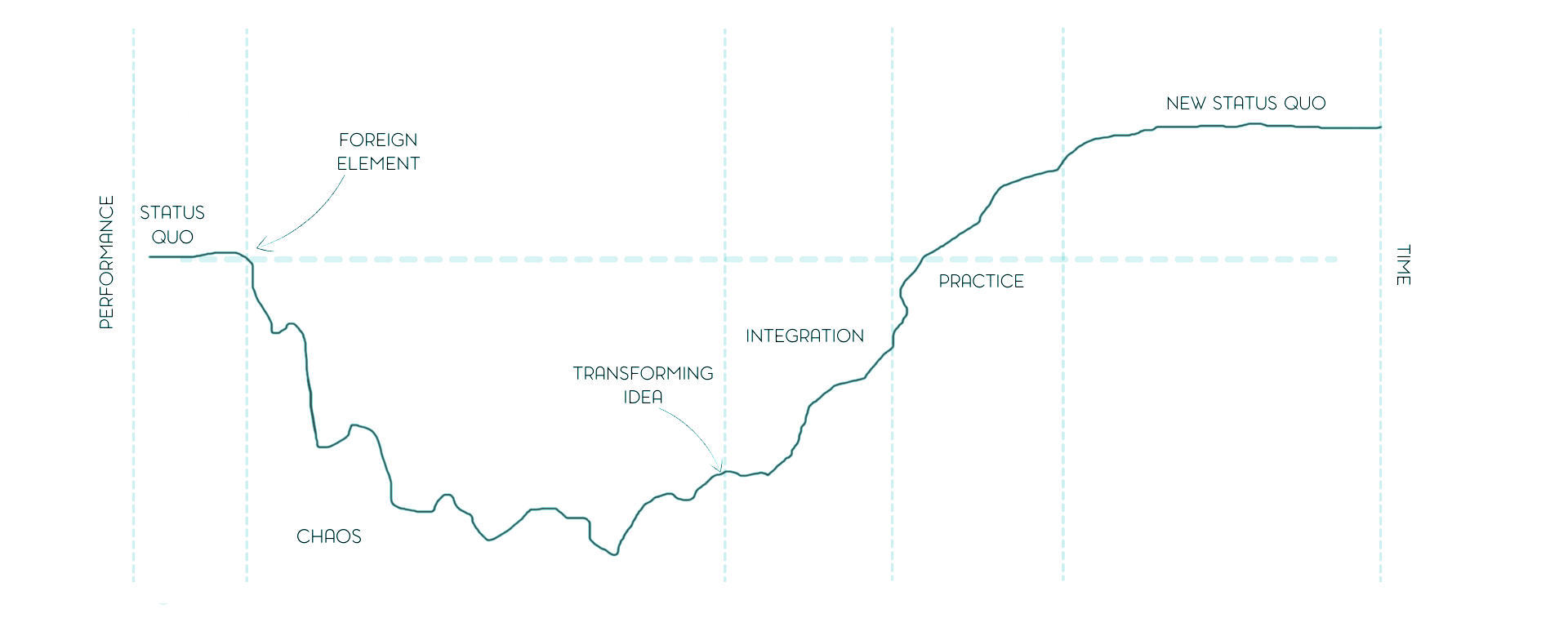
If you have ever tried to set up a Security Incident Response Team (SIRT) function in a small organisation, you will know that it is not about security, incidents, or even teams. It is about humans behaving badly under stress. Enter the Satir Change Model, a tool from family therapy that has no right working in cybersecurity, and yet works better than most “cyber resilience frameworks”. Her five-stage model maps beautifully onto what happens when a small organisation suddenly decides to “get serious about incident response”. Building a SIRT is not about defeating chaos; it is about becoming fluent in it. And once you have done that, “It cannot get any worse” stops being a threat and starts being the team motto making people laugh, sending extra oxygen to their brain. ...