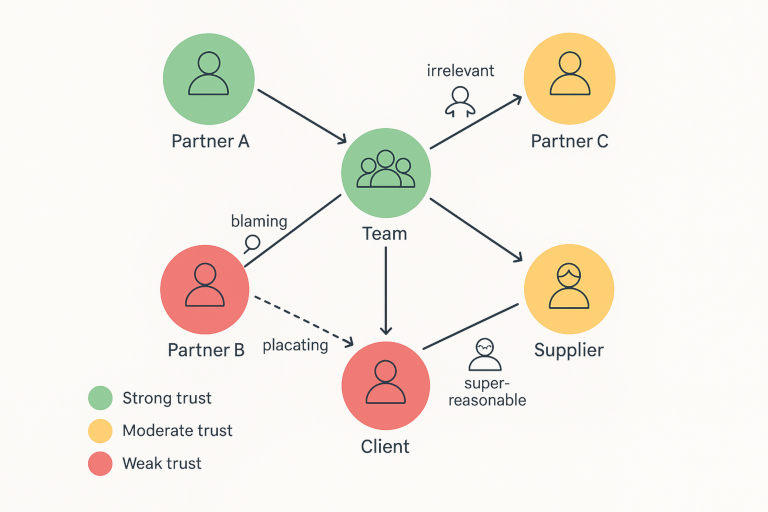
Announcing the UU Power & Light Simulator version 0.1.alpha: Teaching OT security without exploding any turbines
There’s a fundamental problem with learning operational technology security: the things you need to test are the things you absolutely must not break. This creates what educational theorists call “a bit of a pickle” and what facility operators call “no, you’re definitely not touching the production turbines with your laptop.” It’s rather like learning to defuse bombs. The theory is straightforward, the practise is somewhat more stressful, and mistakes tend to be memorable for everyone in the vicinity. In OT security, mistakes might not result in explosions (usually), but they can shut down production, trigger safety systems, or cause equipment damage. These outcomes are suboptimal for learning environments and remarkably unpopular with operations teams who prefer their turbines spinning at correct speeds rather than serving as expensive educational exhibits. ...